Portal:AOL-Files/Articles/AIM Jacking on Macintosh Systems
| AOL-Files | Articles | Downloads | FDO91 | |
(Originally by AOL-Files staff member Tau 2001-02-21, Updated: 2001-02-25)
Many may remember the PC indent exploit that also allowed users to jack AOL Instant Messenger screen names. This was accomplished by changing the language code using the uni_next_atom_typed atom. Unbeknownst to many, this exploit still exists on Macintosh systems and Hypah has been making the most of it.
When AOL patched the PC exploit they basically added a few lines of code to the registration process that instructed the screen name be sent back and canceled if it included the language code atom. However, on Mac AOL 2.7 the token structure is completely different. When AOL patched the PC exploit, they did not patch the Macintosh system. This is ironic, because when BMB discovered how to steal AIMs on PC's, he did it the same way that Hypah originally did on Macintosh: by changing the language code.
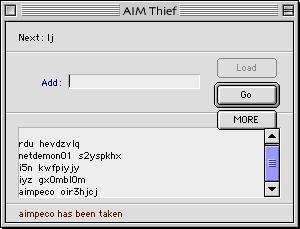
AIM jacking has been occurring on Macintoshs since its discovery by Hypah in April 2000. Not until recently has this greatly affected anyone because not many on Macs know how to do it. Hypah, greatly disturbed by the rising number of people bragging over their "elite" three character AIM screen names, decided to take action. Last Sunday, February 17th, 2001, Hypah began jacking every three character AIM name that could be jacked.
His program would generate each AIM then test to see if it could be jacked. Two restrictions were that the name had to be less than ten characters and it could not have been an AOL screen name within the past six months. Then he would try to jack the AIM. This was done by sending a language code plus an AIM name that would together make up the stolen name. For example, if he wanted to steal the AIM screen name "abc" he would send the language code "ab" and "c" as the AIM screen name.
If "c" was not an existing name on AIM then he could steal the name. When AOL registered the name it combined the language code and the AIM name that he sent. In this case it would be "abc". If that way did not work, he could also send the language code "a " (note the space after 'a') and "bc" as the AIM name. Since no one or two letter screen name exist on AIM, he could make any name except as long as it met the restrictions stated above.
In two days, Hypah jacked 4,751 three character screenname. However, all of these now exist in a state of purgatory. After each screen name was verified, he canceled the registration process. In this way, all of the names that went through to the system were flagged as taken, but the account was never created. Every name has a random passwords as well.
This exploit is still active.